Originally published at: What is Network Automation? | Indeni
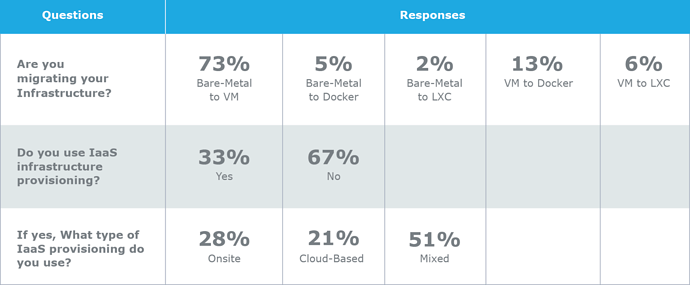
It is very hard to keep up with technology trends, especially if you are a network or security professional. Networks are complex, and mistakes are an inherent fact of human life. In our recent automation survey individual contributors and managers agree technology has outpaced our ability to manage the network - we need automation. Unfortunately our industry has done an impeccable job confusing everyone with acronyms and “new” technologies. Let’s use the next 5 minutes to clarify what network automation is, and how you can use it.
Network Automation Definition
Automation is the process of completing a task or activity without human intervention. When applied to network devices, such as firewalls, routers or switches, automation refers to the completion of tasks such as validating configuration settings, cluster availability, enabling or disabling features to deploying new services without human intervention.Task automation scale
Every organization has different risk tolerances. Here is a simple graph to help guide a discussion around task automation in your internal team. It is possible to automate a range of activities from very low risk and lower complexity, to high risk and high complexity.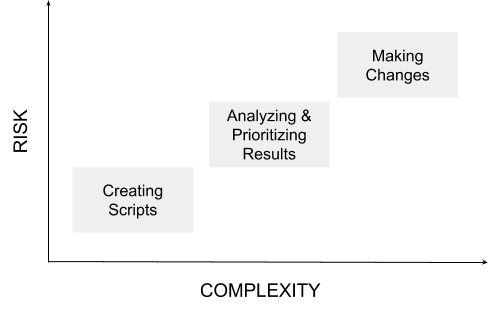
Network tasks to automate in 2018
1. Creating scripts- Commands to use when extracting data
- Parsing data returned from scripts
- Processing and analyzing device data
Let’s break these down further:
1. Create scripts for networking devices 
In order to extract data from a network device you have to understand the protocols it uses or if it has one, the application programming interface (API). Unlike applications and servers, networking gear very rarely has a programmable interface. What is an API? Here is a great description from ProgrammableWeb:“An API is very much the same thing as a UI, except that it is geared for consumption by software instead of humans. This is why APIs are often explained in the mainstream media as a technology that allows applications (software programs) to talk to one another. In this context, the terms “software,” “applications,” “machines” and “computers” are virtually interchangeable. For example, APIs are often discussed as being machine-readable interfaces (versus human-readable).” From this article: APIs Are Like User Interfaces–Just With Different Users in Mind.
Without a well documented programming interface, it is very difficult to know how to extract data, parse or process data from networking devices, regardless if the commands are run proactively or reactively.
2. Prioritizing issues uncovered by data 
Regardless if your environment is on-premises, cloud based, or a hybrid of the two, single vendor solutions are complex and interdependencies exist between them. For example if network performance is degrading, the culprit could be a single configuration, combination of the configurations, and/or connectivity dropping between devices. It takes a subject matter expert with years of experience to understand the implications of situations such as:- What happens when I enable or disable this feature?
- If there is a spike in memory usage, is this a cause for concern?
- When comparing two data trend lines, should they be correlated? Is there a potential problem on the horizon?
3. Implement changes to fix issues
Knowing how to fix a problem is an art, as much as it is a science. It would be more of a science if documentation was always up to date. To get to a state where the network is self-operating humans need to know how to make changes first. Once we know how to make a change, only then can we teach a machine to perform the task without intervention. Machines unlike humans are very good at following directions! In a recent survey by GNS3 and Indeni, it was interesting to see that fewer professionals are implementing automation here than you would guess.For those of us who haven’t programmed our systems to be self operating yet, you can start collecting this information from your team and document runbooks. From the same Network Security Automation survey mentioned above, of those using runbooks, 87% of respondents found them effective to lower cost and increase productivity.
How to get started
If you are just getting started with network automation, start by validating that your network and security devices are set up and working as intended:- Are [Palo Alto Networks, Cisco, Juniper, etc.] best practices are in place?
- Do I have redundancy / cluster availability?
- Have I followed compliance best practices?
- Have I followed security best practices?
If you found this article helpful please share on social media by clicking the share links at the top of this page. Thanks!