Back in December of last year, Palo Alto Networks published PAN-SA-2017-0027 in response to CVE-2017-15944. This was deemed a critical vulnerability across many PAN-OS versions and in January Palo Alto Networks sent an emailed titled “Urgent action recommended regarding recent security advisory”. In that email, the vendor urged customers to update to non-vulnerable versions and implement tighter security controls around their devices’ management interfaces.
Now, four months after Palo Alto Networks’ email, Royce Davis of ServiceNow has shown how easy it is to exploit this vulnerability. This is done with the help of a new Metasploit module created by Philip Pettersson. The new module has drastically lowered the bar for exploitation of this vulnerability.
Royce’s post prompted us to review our data to determine how well have Palo Alto Networks customers followed the guidelines in the email from January. Unfortunately, we’ve discovered that one sixth of all joint Indeni and Palo Alto Networks customers have still not patched all of their affected firewalls. We will be sending a reminder email to our own customers but we are also using this opportunity to remind customers that this vulnerability should not be ignored.
Please, identify all the devices that haven’t yet been patched and do so as soon as possible. The new Metasploit module means that any “script kiddie” can do it.
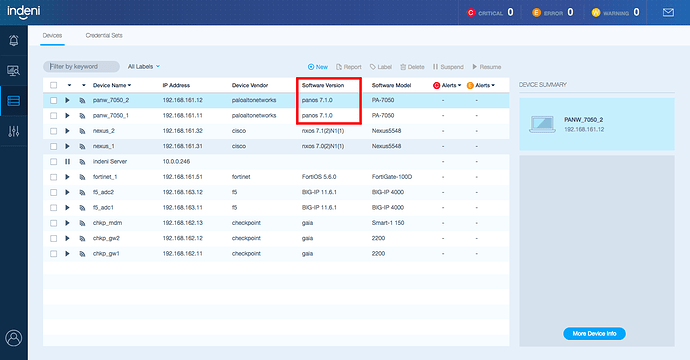
Indeni users can easily identify affected devices by reviewing the Devices tab and the specific versions of PAN-OS in use: