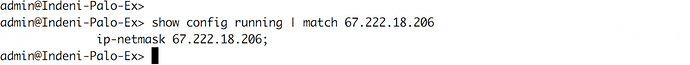Originally published at: Palo Alto Networks CLI Tips | Indeni
Welcome to the Palo Alto Networks
Palo Alto Networks has created an excellent security ecosystem which includes cloud, perimeter/network edge, and endpoint solutions. Amongst the company’s product portfolio is a range of next-generation firewalls that provides customers with an industry-leading security solution. These next-generation firewalls contain a multitude of configuration and endless security subscriptions options that empower customers to protect their infrastructure from port attacks,protocol attacks, and advanced persistent threats (APTs).
With this information in mind, the versatility of this next-generation firewall will result in customers achieving value, return on investment (ROI), and an increased security posture. Consequently, the frequency of usage of this security tool will increase. Even more, business personnel, especially information security professionals, should become familiar with this security platform. This blog post will provide tips to expedite effectiveness when utilizing the CLI for personnel new or familiar with the Palo Alto Networks firewalls. Let us dive in to the CLI.
Accessing the CLI of your Palo Alto Networks next-generation firewall
A user can access first-time configurations of Palo Alto Networks' next-generation firewalls via CLI by connecting to the Ethernet management interface which is preconfigured with the IP address 192.168.1.1 and have SSH services enabled both by default. Additionally, the next-generation firewalls have a console port which a user can utilize for direct serial connectivity. Once the desired access method is utilized, the default credentials for administration are username admin and password admin.Note: For the physical console connection via your designated terminal program, please utilize the following information: Baud Rate 9600 / Data Bits 8 / Parity None / Stop Bits 1 / Flow Control None
Note: A warning will be displayed until the default password is changed
The Mode-Us Operandi
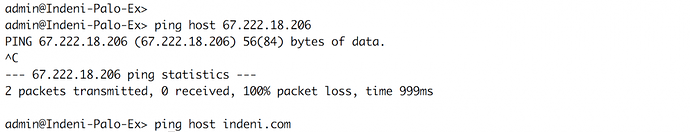
Once you have entered your credentials to gain access to the CLI for your next-generation firewalls, you are able to operate in two modes (according to the privileges assigned to the account). They are the Operational mode and the Configuration mode.Within the Operational mode, the administrator can enter commands to perform pings to the following:
- A designated IP address
- A website address or your default gateway
- Perform a packet capture
- Show running command on candidate configuration
Example for how to view the running configuration or match a condition in the configuration: show config running or show config running | match 67.222.18.206
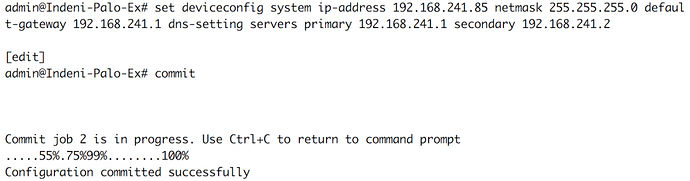
Within the Configuration mode, the administrator can enter commands to update general system settings, security policies, etc. in the candidate configuration. While in Operational mode, the administrator would type and enter configure in the CLI to access Configuration mode. After adding configuration(s) to the while in this mode, the administrator would type and enter commit to update the running configuration.
A user can also execute Operational Commands while in Configuration mode by prepending run to a command.
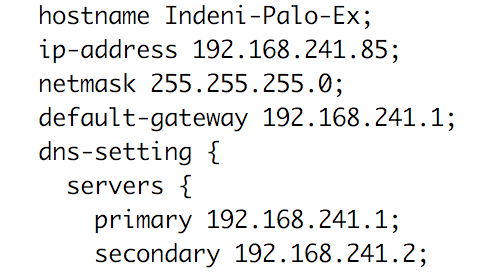
Example for how to set the next-generation firewall’s management IP address information and the primary and secondary DNS servers: While in Configuration mode. set deviceconfig system ip-address 192.168.241.85 netmask 255.255.255.0 default-gateway 192.168.241.1 dns-setting servers primary 192.168.241.1 secondary 192.168.241.2
Enter commit to update the running configuration.
Ex for how to ping from the Configuration mode: run ping host indeni.com
Ex for how to view the running configuration from the Configuration mode: show
The Answer is in the ?
As you become more familiar with the commands in the Operation mode and Configuration mode, you will be able to input commands and the required syntax. Until memorization of the commands is completed, the administrator can type ? (question mark) and the available commands and required syntax will be displayed.Keeping a Tab on Things
Even more, the CLI has an option for saving keystrokes of the whole command. The administrator can hit the Tab to complete commands.Set It Until You Get It
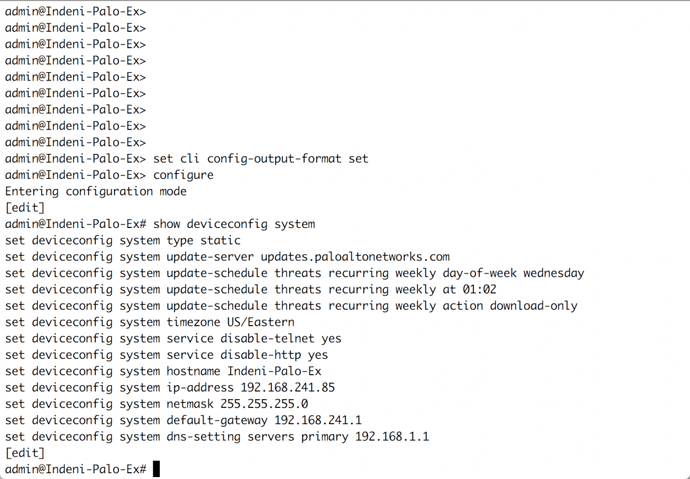
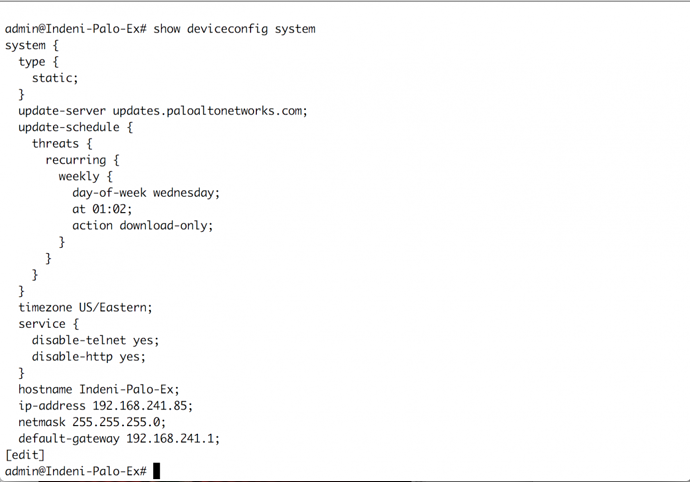
Whether immediately after logging in or after making updates, an administrator has to check the configuration of the next-generation firewall. The default output for the configuration is xml format, however you can change the configuration format. Viewing the configuration in this output format may take time to understand as you are learning its grouping. Thankfully, the administrator can expedite understanding of the overall configuration by changing the output format. The options available for the output format are json, set, and xml.The set output format is a great option reviewing the configuration and for adding or editing lines in the configuration.
Example for how to change the set output format for the configuration:
While in the Operational mode, set cli config-output-format set
Enter configure to elevate to Configuration mode
Enter show to view the running configuration
(Deviceconfig in set output format)
(Deviceconfig in xml output format)
Test and See
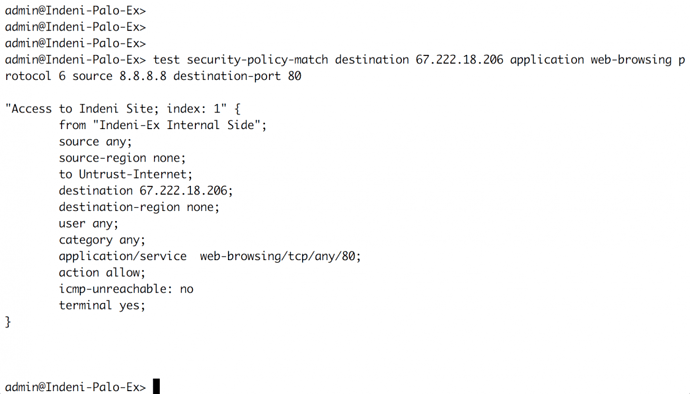
Following the completion of a configuration for the next-generation firewall, the administrator should conduct testing to verify that traffic will operate as intended in the production environment. Palo Alto Networks has included a command to display how the firewall will respond to certain criteria—test. The test command supports testing for security policies, NAT policies, routing, and other configuration options.Example for how to verify if traffic will be allowed to a website via a security policy (web/port 80 to the Indeni website):
While in the Operational mode, test security-policy-match destination 67.222.18.206 application web-browsing protocol 6 source 8.8.8.8 destination-port 80
Continue On
The Palo Alto Networks next-generation firewall is a powerful tool that is very effective against security threats. These CLI tips are here to empower administrators to be effective when operating the next-generation firewall’s CLI and to keep administrators from looking silly. Take this information and continue on your path to becoming an even better user and administrator of Palo Alto Networks next-generation firewalls.This blog post was written by Indeni Crowd community member, Paul Carter. More writers are wanted! Learn how to contribute your industry expertise here.