Originally published at: Indeni 6.4 is Now Generally Available | Indeni
We are very excited to announce that Indeni 6.4 is available for download. This release brings many valuable features including:
- Role-based Access Control
- Change User Preference for LDAP Authenticated Users
- Rules Visibility
- New Knowledge - Check Point CloudGuard Support
Role-based Access Control
Role-based access control (RBAC) is the latest feature built into Indeni Rel 6.4. It is common for large enterprises to have operations teams that focus on the ongoing operations of the network, and dedicated IT teams that focus on security and networking functions. Administrators can now assign read-only roles to operators responsible for Indeni day to day operations. Support for RBAC is key to ensuring that administrators have tools to prevent unauthorized changes to the Indeni system.Read-only Role
The administrator role can control all aspects of the system. Users with read-only role have limited functions. Functions that are not permitted are hidden. Users with read-only privilege cannot perform the following functions:
- System administration Users cannot configure LDAP and integration functions.
- User administration Although read-only users cannot add, delete or change user accounts information, they can change the settings when it comes to receiving issues preference via email based on the criticality of the issue.
- Device administration Users cannot add or remove devices, configure device settings including device credentials, device names and IP addresses. They cannot remove or modify labels. They cannot configure backups. However, they can put a device in suspend mode and resume operations of a device.
- Issue administration Users cannot configure the alert setting such as changing thresholds, severity or disabling rules. They can however archive issues.
For more information, please refer to the Indeni 6.x User Guide - RBAC.
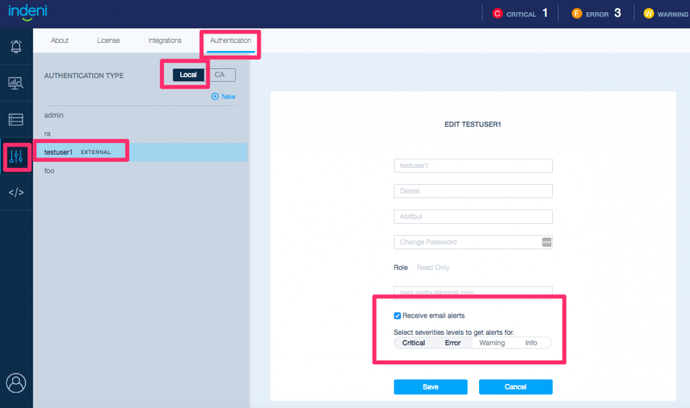
Change User Preference for LDAP Authenticated Users
Authentication can be handled locally by Indeni or by using Microsoft Active Directory service. Users that are authenticated by Active Directory can set what kind of notifications the user should receive based on the criticality of the issues.For more information, please refer to the Indeni 6.4 User Guide - Configuring User Level Privileges.
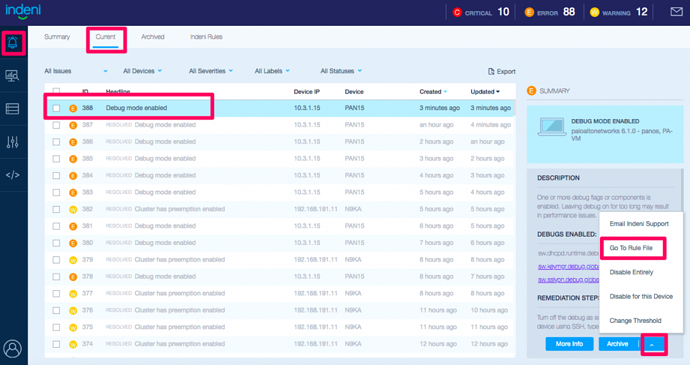
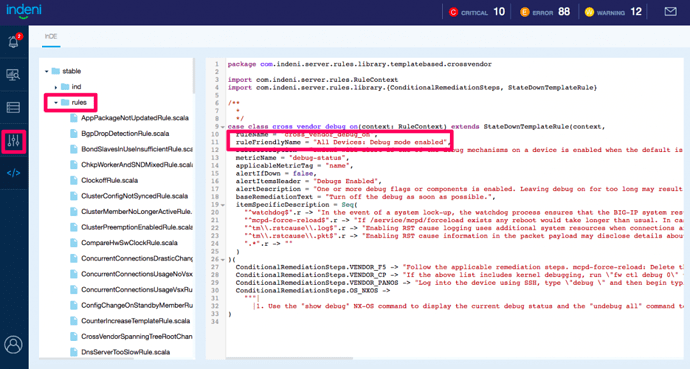
Rules Visibility
We also added the source code for the rules to our developer portal (InDE - Indeni Development Environment).From Issues -> Current, select the issue of interest. In this example, select “Debug mode enabled”, then click on the blue up arrow next to the blue Archive button, then select “Go To Rule File”, Indeni will navigate to the source code of the rule that generates the issue.
New Knowledge – Check Point CloudGuard Support
As enterprises are accelerating cloud adoption, security remains a key concern for many businesses. Customers are deploying Check Point’s CloudGuard security solutions for threat prevention and keeping enterprise cloud applications, infrastructure and data protected from cyberattacks. Indeni automates related Check Point CloudGuard tasks such as ongoing maintenance, high availability validation steps, best practices and much more.If you are looking for ways to extend and protect the value of your Check Point systems on the premise, in the public or private cloud, download Indeni today and join our community Indeni Crowd to engage with other certified Check Point experts.