Originally published at: Fortinet FortiGate HA (High Availability) Solutions | Indeni
Importance of HA
In this article, we will discuss the importance of HA (High Availability) solutions for your FortiGate firewall(s). We will compare two of the best solutions – VRRP (Virtual Router Redundancy Protocol) and HA using FGCP (FortiGate Cluster Protocol), outlining the pros and cons for each. We will also go through configuration examples.So, let’s begin.
In times when each minute of network disruption can cost the company thousands of dollars, serious businesses tend to have redundant internet links. But in case your router/firewall stops working, having two or more WAN connections is not going to help you much. That’s why it’s a good idea to also have two network devices, working in master/slave mode, where the second unit can take over if the first one fails. That’s why FHRP (First Hop Redundancy Protocols) protocols such as HSRP (Hot Standby Router Protocol) and VRRP were invented. On the other hand, firewall vendors have developed another means of providing the hardware redundancy – High Availability. So, let’s get some facts straight.
VRRP: Virtual Router Redundancy Protocol
VRRP history
VRRP was developed as a non-vendor specific response to Cisco’s proprietary HSRP protocol. These protocols work under the same principals, except that you can use VRRP between two different vendors, while with HSRP you must go with Cisco.VRRP concept
VRRP uses the concept of virtual IP address and MAC address shared by master and slave devices. Master unit will use the virtual IP address as its interface IP address but if it fails, the unit operating in slave mode will take its place, becoming the master itself and using the same virtual IP address. VRRP is configured by creating a VRRP group with two or more FortiGates. With VRRP, one device can be a FortiGate firewall, but the other device can be a simple router (that supports VRRP of course).In addition to all this, you can setup VRRP to load balance the traffic between VRRP participants. That way you won’t have members of the VRRP group sitting idle.
VRRP operations
Like most of the network protocols, VRRP uses advertisements sent regularly between the participants. There are two types of advertisements – hello and dead interval packets. Default VRRP timers change from vendor to vendor. FortiGate has a 1 second hello timer and a 3 second keep alive timer. Hello packets are being sent on regular one second intervals from the master. Slave will not attempt to become the primary unit until it stops receiving hello messages. After the default three seconds for the dead interval expire, slave will decide the master has failed and it will take over.FGCP HA – High Availability with FortiGate Cluster Protocol
WHAT is HA?
High Availability is a FortiGate specific solution for providing redundancy. HA uses FGCP. Essentially, HA functions similar to VRRP, but one of the main differences is that you absolutely must have two same FortiGate models to achieve HA. When you join your firewalls to a cluster they will sync their configurations and function as one device, providing failover and load balancing the traffic if needed.Forming a cluster
To join FortiGate units to a cluster, participants must have the same model, firmware, and hardware (same types or number of modules, etc.). Every cluster will have a primary FortiGate unit and one or more (up to three) secondary units.FGCP concept
Like VRRP, HA will assign the virtual MAC addresses to cluster units, using gratuitous ARP to communicate between cluster units. By tuning the timers, FortiGate failover time can be less than one second – if set properly and in ideal conditions.FGCP requirements
Another important thing to note here is that you will need additional networking equipment to configure HA. It is necessary to connect another switch between the HA cluster members and the internet (NTD – Network Termination Device), thus adding another single point of failure. This can be mitigated by introducing another switch, possibly using another VRRP between to create full redundancy. That means you need another two networking devices to implement HA properly and up to four (because you need another switch or a pair between firewalls and LAN). This can pile up expenses quite quickly.Let’s get to some configuration examples. First, we will cover VRRP.
VRRP configuration
Master unit configuration:config system interfaceJamaica # config system interface
Jamaica (interface) # edit port4
new entry ‘port4’ added
Jamaica (port4) # set vrrp-virtual-mac enable
Jamaica (port4) # config vrrp
Jamaica (vrrp) # edit 100
new entry ‘100’ added
Jamaica (100) # set vrip 172.16.50.100
Jamaica (100) # set priority 255
Slave unit configuration:
Cuba # config system interface
Cuba (interface) # edit port4
new entry ‘port4’ added
Cuba (port4) # set vrrp-virtual-mac enable
Cuba (port4) # config vrrp
Cuba (vrrp) # edit 100
new entry ‘100’ added
Cuba (100) # set vrip 172.16.50.100
Cuba (100) # set priority 50
Ok, let’s explain. We are using port 4 on both FortiGates for VRRP. First, we assigned a virtual MAC address to this port. Virtual MAC address enable on the interface can fasten the convergence during the failover since devices on the LAN don’t have to learn the MAC address of the failover router.
Then we got into VRRP configuration mode and configured VRRP group id of 100 on port4. We then configured the virtual IP address 172.16.50.100 to be used on this port and lastly we set the priority. Primary unit has higher priority of 250 making it the master. Unlike Cisco, preemption is enabled by default so you don’t have to worry about it.
Load balancing VRRP configuration is similar enough. Only difference is that we will introduce another group id and another virtual IP address.
VRRP Load Balancing configuration
config system interfaceJamaica # config system interface
Jamaica (interface) # edit port4
new entry ‘port4’ added
Jamaica (port4) # set vrrp-virtual-mac enable
Jamaica (port4) # config vrrp
Jamaica (vrrp) # edit 100
new entry ‘100’ added
Jamaica (100) # set vrip 172.16.50.100
Jamaica (100) # set priority 255
Jamaica (100)# end
Jamaica (vrrp) # edit 200
new entry ‘200’ added
Jamaica (200) # set vrip 172.16.50.200
Jamaica (200)# set priority 50
Slave unit configuration:
Cuba # config system interface Cuba (interface) # edit port4 new entry 'port4' added Cuba (port4) # set vrrp-virtual-mac enable Cuba (port4) # config vrrp Cuba (vrrp) # edit 100 new entry '100' added Cuba (100) # set vrip 172.16.50.100 Cuba (100) # set priority 50 Cuba (100) # end Cuba (vrrp) # edit 200 new entry '200' added Cuba (200) # set vrip 172.16.50.200 Cuba (200) # set priority 255 Cuba (200) # end
Now we configured another virtual group with another virtual IP address. One FortiGate is the master of one group and vice versa. That way, both FortiGates will load balance the traffic. You now need two default routes. One will use 172.16.50.100 as a next hop and the other one 172.16.50.200. If one FortiGate fails, the other one will become the master for both groups. And now you don’t have an idle unit sitting still. Pretty cool!
VRRP Useful commands
There are some useful commands for fine tuning your VRRP setup. You alter hello timers with the adv-interval option. You can set values from 1 to 255 seconds, and with 1 second being the minimum and also the default timer, it won’t really speed up your failover interval. More useful option is altering your start-time interval – basically your dead timer. The default is 3 seconds, but it can be lowered to 1. The maximum start-time value is 255 seconds.HA – High Availability configuration
Let’s get to our HA configuration.Prior to the configuration, it’s necessary to properly connect your devices. If your firewall has dedicated HA heartbeat interfaces then of course use those. If not, you can use any unused interfaces. Power on both devices and they will automatically negotiate and chose the primary and secondary unit.
First, we want to change the hostname, so we can easily distinguish the units.
Jamaica # config system glob Jamaica (global) # set host Jamaica1 Jamaica # config system glob Jamaica (global) # set host Jamaica2
Now we need to choose the HA mode. Active-passive is being used to provide failover only and active-active is providing load-balancing on top of that.
Jamaica1 # config system ha Jamaica1 (ha) # set mode active-passive Jamaica1 (ha) # set group-name Cluster Jamaica1 (ha) # set password P@ssw0rd
We also defined the clusters name, conveniently Cluster and the extremely hard to crack password – P@ssw0rd. On the other FortiGate, repeat the commands.
Jamaica2 # config system ha Jamaica2 (ha) # set mode active-passive Jamaica2 (ha) # set group-name Cluster Jamaica2 (ha) # set password P@ssw0rd
Firewalls will now negotiate to choose the primary one. After they form an HA cluster FortiGates synchronize the configuration and act as a single unit providing redundancy when one of them fails.
Now, let’s give these interfaces IP addresses and connect them to the network.
Jamaica1 # config system int Jamaica 1 (interface) # edit port1 new entry 'port1' added Jamaica (interface) Jamaica1 (port1) # set ip 192.168.134.25/24 Jamaica1 (port1) # next Jamaica1 (interface) # edit port2 Jamaica1 (port2) # set ip 192.168.135.25/24 Jamaica1 (port2) # end Jamaica1 (port2) # config router static Jamaica1 (static) # edit 1 Jamaica1 (1) # set dst 0.0.0.0 0.0.0.0 Jamaica1 (1) # set gateway 192.168.135.25 set device port1 Jamaica1 (1) # next Jamaica1 (static) # edit 2 Jamaica1 (2) # set gateway 192.168.136.25 set device port2 Jamaica1 (2) # end
That was easy enough. Now your FortiGates work in HA mode.
If you want to load balance system-hungry firewall processes, you can also enable active-active mode and have both firewalls actively participating in your network.
Conclusion
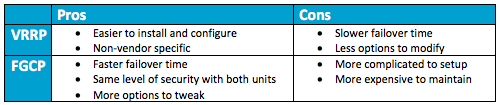
We’ve demonstrated basic configurations for providing redundancy between your firewalls. Now, let’s compare FGCP and VRRP. What are the pros and cons of these protocols and how do you determine which one to use?VRRP is an open vendor protocol which means you can connect FortiGate and any other network device that supports VRRP. The downside of this is that if the other unit is not FortiGate, all the advanced security features you have on the FortiGate firewall not work.
On the other hand, FGCP demands two exact same firewalls with the same firmware and hardware modules. Also, you need two switches, one between FortiGates and LAN and one between FortiGates and WAN. So, if you continue following the redundancy trend, now you will need four switches with some kind of VRRP between each pair.
VRRP
We hope this was informative for you! Head over the to Indeni Crowd to continue the discussion on Fortigate HA solutions.
Thank you to Filip Knezevic for contributing this article

