Originally published at: Fortigate’s FortiDDoS Review | Indeni
DDoS attacks are becoming a plague for companies that rely on the Internet to operate their business. Scripts to operate a DDoS attack are easily accessible and can make your Internet connection completely unusable.
DDoS attacks use “armies” of malware-infected machines to flood the servers with un-legitimate traffic. Soon the server’s resources are entirely depleted making it unavailable for the legitimate users.
In our last blog we’ve presented the Checkpoint’s DDoS attack mitigation solution, and in this article, we investigate Fortinet’s FortiDDoS. The Primary principle is similar: FortiDDoS also utilizes dedicated hardware on site with in-cloud protection as a backup. While Checkpoint is using Radware’s cloud solution, Fortigate uses Verisign DDoS cloud solution. We also discuss a selection of differentiating features for FortiDDos.
FortiDDoS Characteristics
FortiDDoS comes with different models, suitable for small, medium and large enterprises. Fortigate states a device can stop a DDoS attack in a matter of seconds. FortiDDoS has up to 36 Gbps throughput and is capable of defending from Layer 3, Layer 4 and Layer 7 attacks. FortiDDoS can protect its users from known attacks in addition to unknown attacks, called zero-day attacks. It uses behavior-based DDoS protection, so it doesn’t need to rely on signature files and, according to Fortigate, it provides a minimal amount of false-positive detection. It is also capable of monitoring thousands of different parameters at the same time. FortiDDoS can protect its users from every type of DDoS - volumetric attacks, application-based attacks, SSL/HTTPS attacks.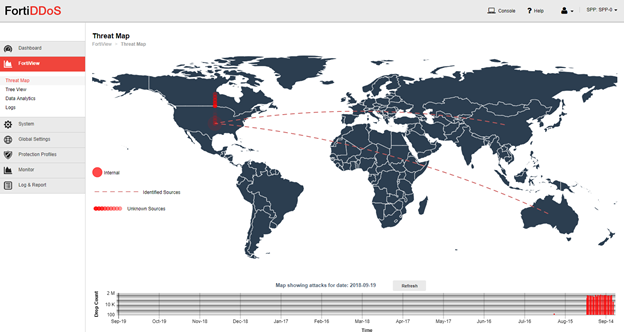
Customizable ASIC Approach
Fortigate is uses its proprietary Application Specific Integrated Circuit Traffic Processors (FortiASIC-TP2) to provide quick and effective protection from the ever-evolving threat of DDoS attacks. FortiDDoS surgically removes Network and Application layer attacks, allowing only legitimate traffic flow to the client.Fortinet is the only company using 100 % custom ASIC approach for their DDoS appliances, protecting the users from both known and zero-day attacks. By using ASIC, FortiDDoS doesn’t rely on signature files to be updated. However, it’s computing and comparing thousands of traffic parameters, recognizing the patterns or both normal and abnormal traffic flows. Both inbound and outbound traffic have guaranteed protection.
Fortigate FortiDDoS claims a nearly 40% lower latency than other solutions and that it detects anomalies faster than any other product on the market.
How does it work?
FortiDDoS initially attempts to stop the attack using its behavior-based approach. If the attack is too significant and the device itself is unable to mitigate the attack completely, the traffic redirects to the cloud where it's cleaned from un-legitimate traffic. Similar to the Check Points solution, only the legitimate traffic sends back to the client.So, for example, a whole range of DDoS attack is using manipulation of ACK, RST, and FIN packets, usually never replying the server with ACK packet, to finish the three-way handshake. FortiDDoS understands there was never a connection established and instantly drops the packets as foreign, meaning they have zero impact on the user.
People responsible for the development of FortiDDoS solution are trying hard to ensure servers’ memory, and real-time resources won’t be overwhelmed during the attack. For example, a massive SYN attack over a 10GE link can theoretically generate up to 16 million packets, and FortiDDoS is capable of mitigating up to 24 million packets - completely protecting 10GE links from massive attacks.
Policies For Everyone
One nice touch about FortiDDoS is that you can have different policies for different network segments. Thus, the attack centers into one network segment, not all of them. This aspect of the solution is especially useful for Systems Integrators, Managed Services Providers, ISPs and other companies that have many clients they need to protect, using different policies.Configuring DNS Flood Mitigation Parameters
Here, we have chosen to demonstrate how to set up protection from symmetrical DNS flood attacks which are trying to deplete server’s memory or CPU resources to bring it to a halt. DNS flood attack is a Layer 7 type of an attack and a form of a UDP flood attack since DNS is relying on UDP to provide name resolution.Configuration:
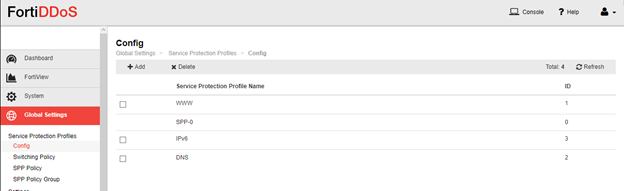
In Global Settings - Service Protection Profiles create SPP for DNS traffic.
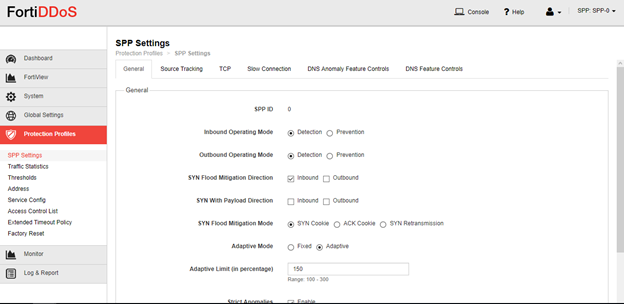
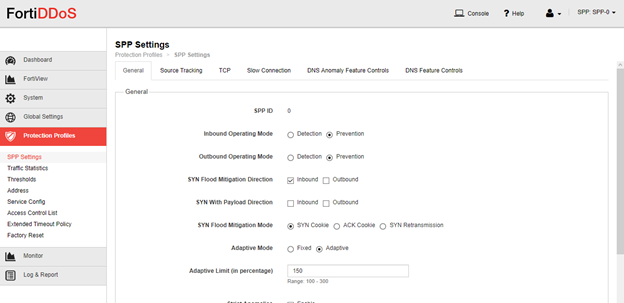
Go to Protection Profiles - SPP settings - General tab and ensure SPP is in Detection mode.
Go to Protection Profiles - SPP settings - DNS Protocol Anomalies tab and enable all anomalies.
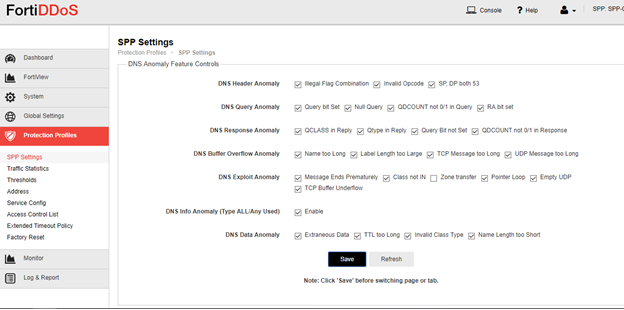 Do the same on DNS Feature Control tab.
Do the same on DNS Feature Control tab.
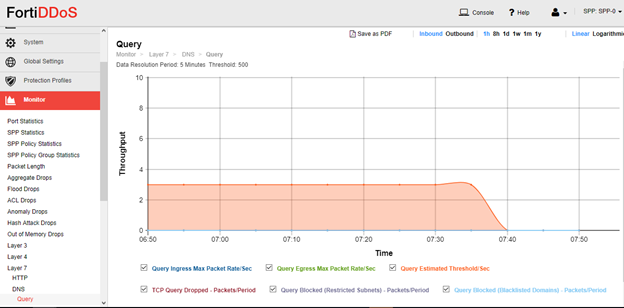
 Go to Monitor Graphs - Layer 7 - DNS and observe accumulation of traffic statistic at least for a full week before switching to Prevention mode.
Go to Monitor Graphs - Layer 7 - DNS and observe accumulation of traffic statistic at least for a full week before switching to Prevention mode.
 Configure thresholds for UDP and TCP rates. First go to Protection Profiles - Traffic Statistics and generate statistics. Afterwards go to Protection Profiles - Thresholds - System Recommendation and generate thresholds.
Configure thresholds for UDP and TCP rates. First go to Protection Profiles - Traffic Statistics and generate statistics. Afterwards go to Protection Profiles - Thresholds - System Recommendation and generate thresholds.
 Go to Protection Profiles - SPP settings - TCP tab and turn on Foreign Packet Validation and Layer 7 Flood.
Go to Protection Profiles - SPP settings - TCP tab and turn on Foreign Packet Validation and Layer 7 Flood.
 Now go to Protection Profiles - SPP Settings - General tab and change to Prevention mode.
Now go to Protection Profiles - SPP Settings - General tab and change to Prevention mode.
 That’s it. Now to test this you only need to be attacked with a DNS flood DDoS attack.
That’s it. Now to test this you only need to be attacked with a DNS flood DDoS attack.
Conclusion
You are probably here, reading this because you’re thinking about purchasing a DDoS attack mitigation solution. Mainly if your company relies on the Internet to operate and each minute of downtime can cause severe financial loss. Fortinet FortiDDoS has some unique features that make it competent on the market. Fortigate states their solution can block the attacks in a matter of seconds. Moreover, the nice thing is you can always grab a demo version and play with it for 30 days.

