I want to create a site to site VPN tunnel between two offices. Has anyone done that before? Would you even recommend that?
Hi Ulrica - Great question!
Yes, you can create a site-to-site VPN tunnel between a Fortinet FortiGate and a pfSense firewall. Please note the following is offered with no warranty and may result in breaking existing configuration. This is tested with devices that are not performing any other role.
Here’s an example configuration of values that have been tested and known to work:
pfSense (running 2.3.2-RELEASE-p1)
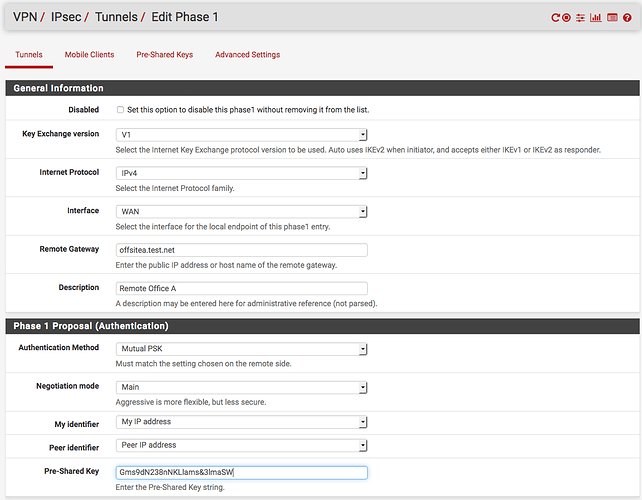
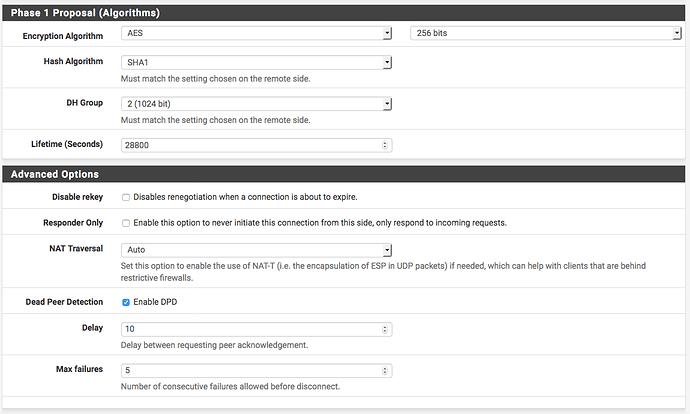
On your pfSense firewall, create a new phase 1 tunnel by going to VPN → IPsec → “Add P1”:
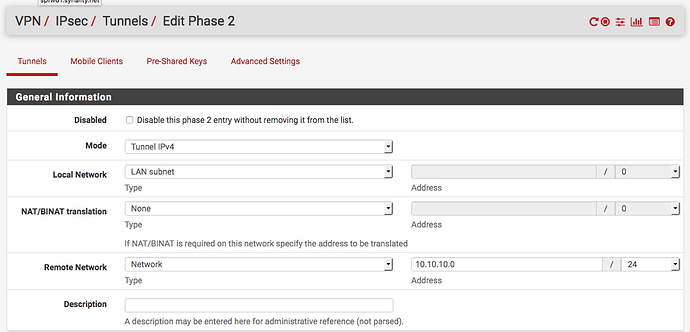
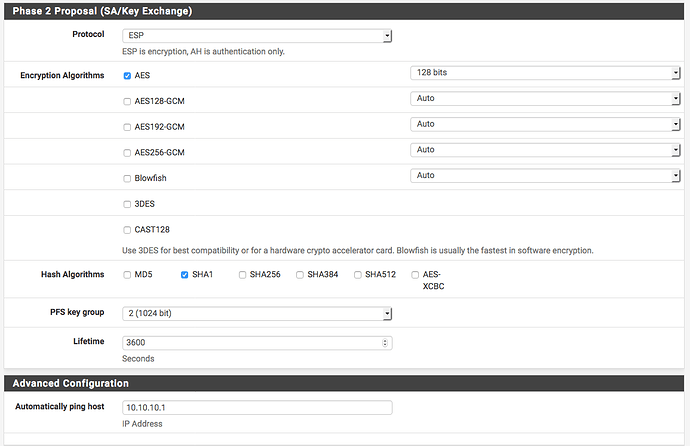
Add a phase 2 selector to the phase 1 tunnel you just created:
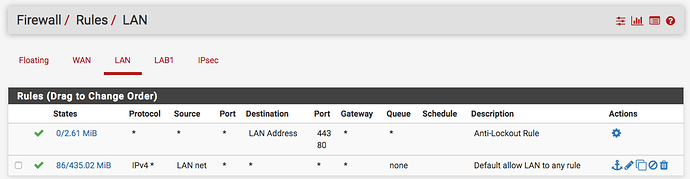
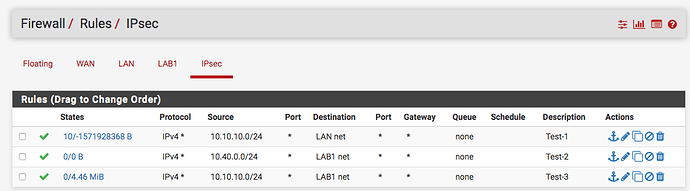
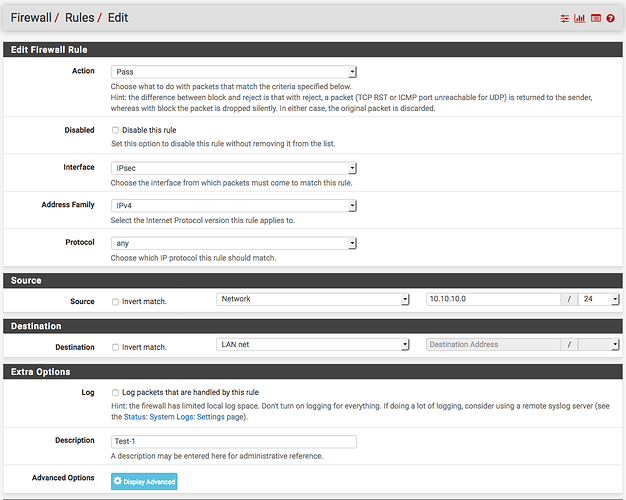
Create a rule to allow traffic inbound from the IPsec tunnel under Firewall → Rules → IPsec
By default pfSense has a rule to allow traffic from the local LAN to anything. That is sufficient to allow traffic to the IPsec tunnel. However, it is always recommended to remove this rule and provision your ACL’s as restricted as you feasibly can to ensure you aren’t allowing unnecessary traffic.
FortiGate (running 5.4.8)
Via CLI (please sanity check and customize for your specific configuration):
config firewall address
edit “Net-Offsite-A-LAN-1”
set subnet 10.10.10.0 255.255.255.0
next
edit “Net-Datacenter-LAN-1”
set subnet 192.168.0.0 255.255.255.0
next
end
config vpn ipsec phase1-interface
edit “datacenter-1”
set interface “wan1”
set keylife 28800
set peertype any
set proposal aes256-sha1
set dpd on-idle
set dhgrp 2
set remote-gw datacenter.test.net
set psksecret Gms9dN238nNKLlams&3lmaSW
set dpd-retryinterval 5
next
end
config vpn ipsec phase2-interface
edit “datacenter-1_1”
set phase1name “datacenter-1”
set proposal aes128-sha1
set dhgrp 2
set auto-negotiate enable
set src-addr-type name
set dst-addr-type name
set keylifeseconds 3600
set src-name “Net-Offsite-A-LAN-1”
set dst-name “Net-Datacenter-LAN-1”
next
end
config firewall policy
edit 0
set srcintf “datacenter-1”
set dstintf “lan”
set srcaddr “Net-Datacenter-LAN-1”
set dstaddr “Net-Offsite-A-LAN-1”
set action accept
set schedule “always”
set service “ALL”
set logtraffic all
next
edit 0
set srcintf “lan”
set dstintf “datacenter-1”
set srcaddr “Net-Offsite-A-LAN-1”
set dstaddr “Net-Datacenter-LAN-1”
set action accept
set schedule “always”
set service “ALL”
set logtraffic all
next
config router static
edit 0
set dstaddr Net-Datacenter-LAN-1
set device “datacenter-1”
next
end
You would need to update the phase-1 interface to match your WAN interface and the policies interface name to match that of your local interface.If you would prefer to do it via the GUI, you can run through the VPN tunnel wizard and configure the settings to match the respective sections above.
Please don’t hesitate to ask if you have any other questions or if I can clarify anything for you.
Hi Chris,
This is super helpful. Doesn’t look trivial at all. Not sure that’s something I want to attempt without support from other experts like yourself 
THANKS!!!