Originally published at: Network Security & Cloud Native Security Infrastructure Automation | Indeni
Indeni Custom Reporting gives you more dynamic engagement with historical data that allows you to quickly visualize trends in order to understand the overall health of your environment. It also gives you an understanding of where your organization falls within Industry Best Practices and Compliancy for greater insights into the health posture of your security infrastructure. You can also schedule your Policy Reports to be sent to your stakeholder daily, weekly, or monthly; ensuring compliancy deadlines are never missed.
Where can I get the Custom Reports?
From the Analytics Tab, select the Custom Report. From there, build your new report with the following steps:- Give it a meaningful name.
- Add a widget.
- Click on edit.
- Select time range of issues you want reported.
- Select devices or labels.
- Select the issues you want to report on.
What reports can I build?
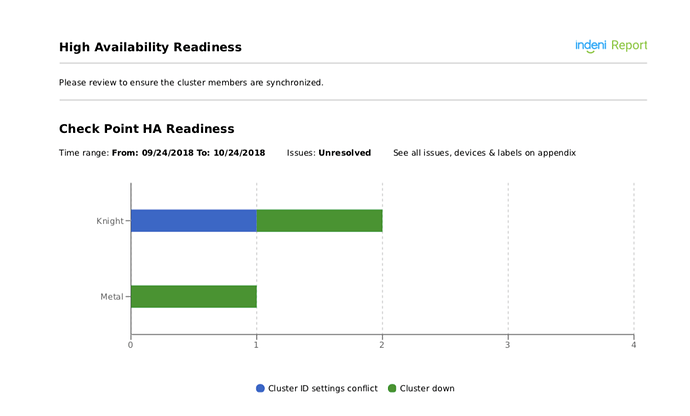
Daily Reports show the list of devices that had issues generated within the last month, and if the issues are still outstanding. This report will help you focus on addressing your most critical issues.High Availability (HA) Configuration Reports are a key element for achieving business continuity 24/7. A highly available infrastructure involves multiple components working together. Gaining insight into the readiness of your HA infrastructure is important to achieving uninterrupted service.
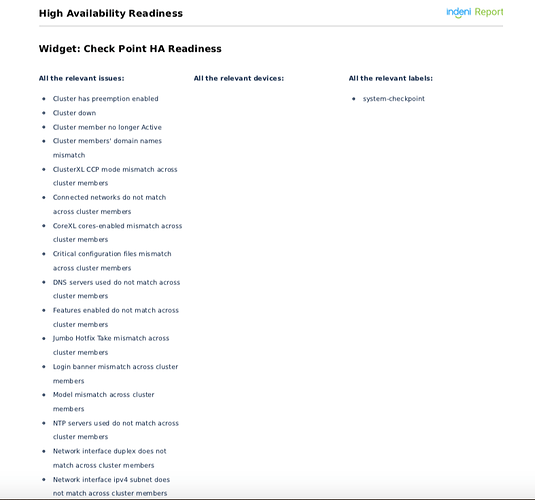
Here are the list of rules used to build the HA Readiness report as shown above.
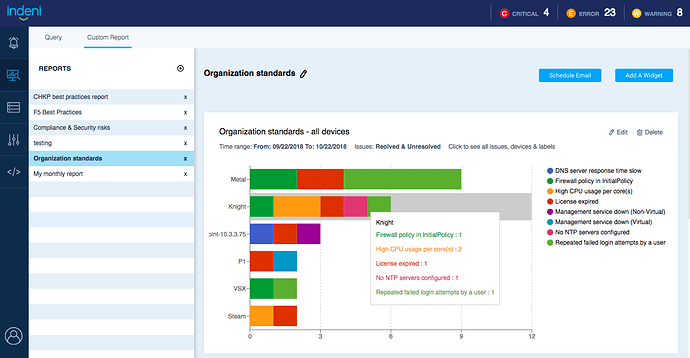
Organization Standards Report are a monthly recurring report that can help you adhere to the company’s “golden” standards for the myriad devices you have. This helps to reduce unnecessary errors from ad-hoc changes.
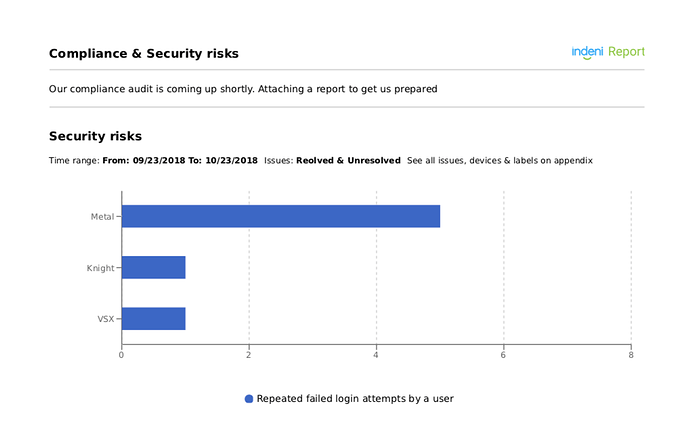
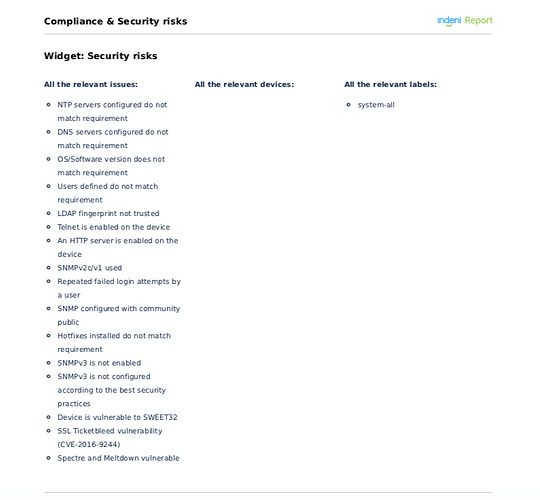
The Compliance & Security Risks Report can be run periodically to prepare for any regulatory audits. These reports can be sent directly to the auditors every month to demonstrate that the best security measures are observed on an ongoing basis.
Here are the list of rules used to build the compliance & security report as shown above.
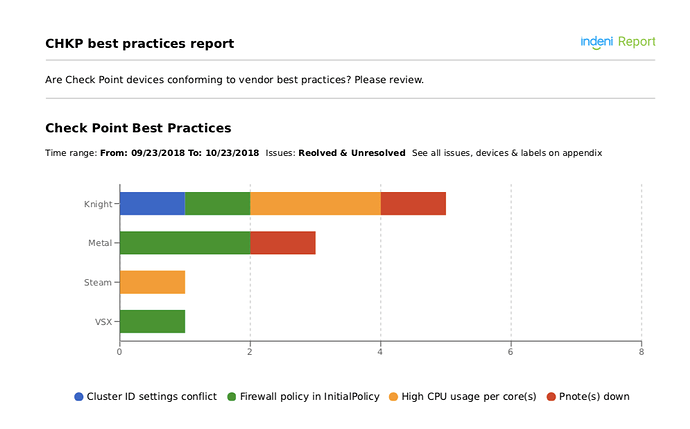
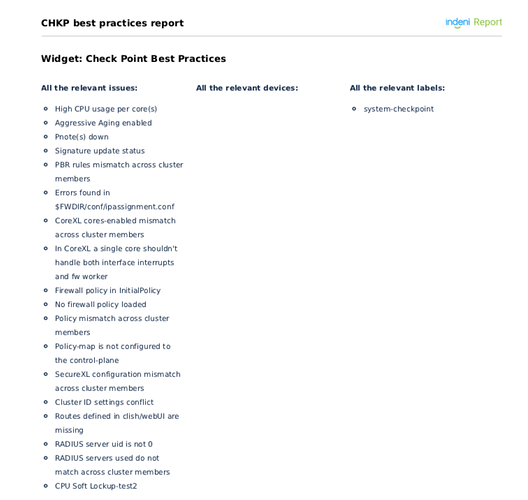
The Vendor Best Practices Report allows engineers to ensure that they are within the recommended operational best practices defined by them. Here is is a sample report for a Check Point devices that helps you gain insight, and gauge, if you are following their recommended best practices.
Here are the list of Check Point best practices rules used to create the report.
If you have any other questions around Custom Reporting feel free to Join our Community discussion and us ask there!